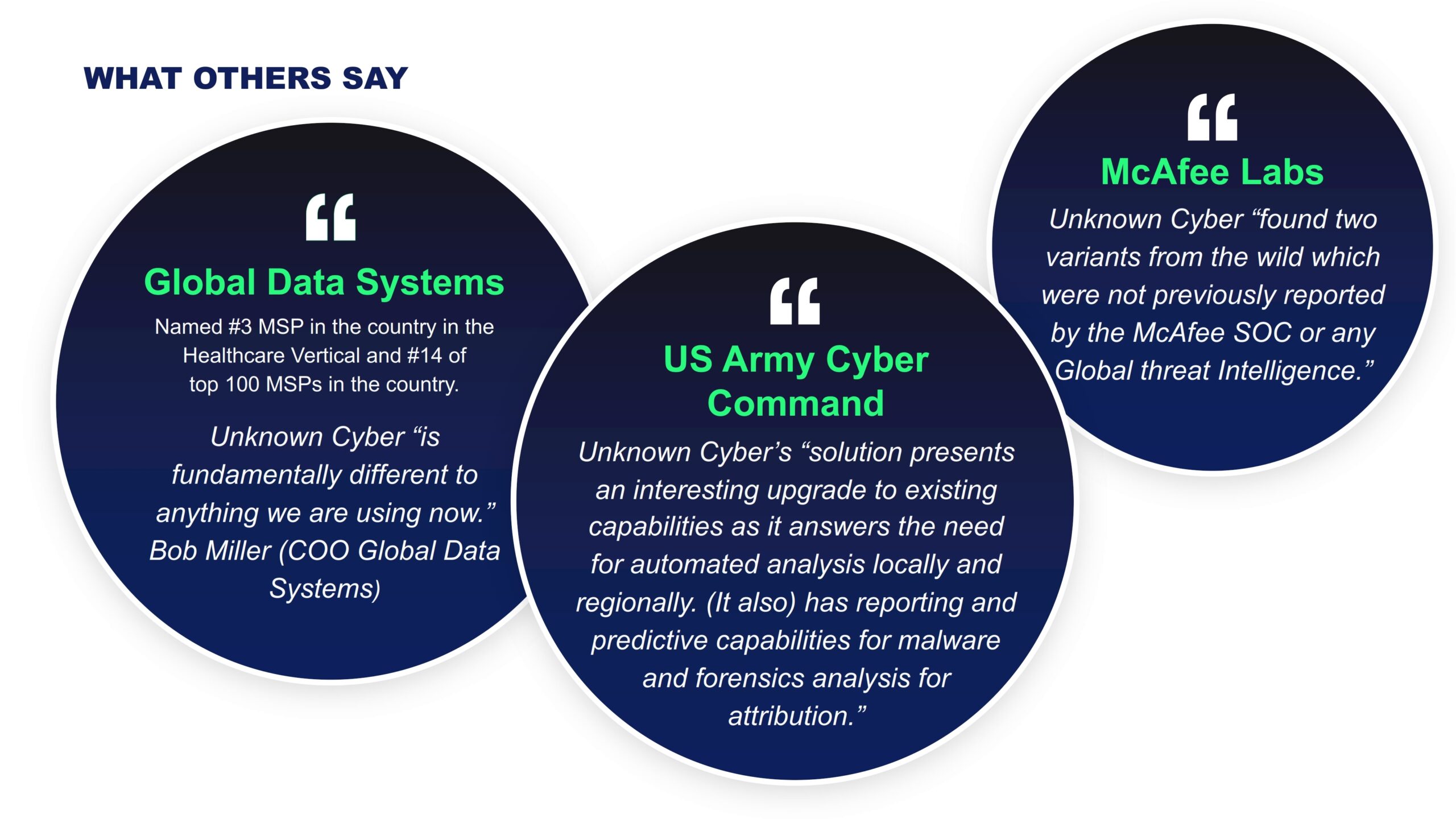
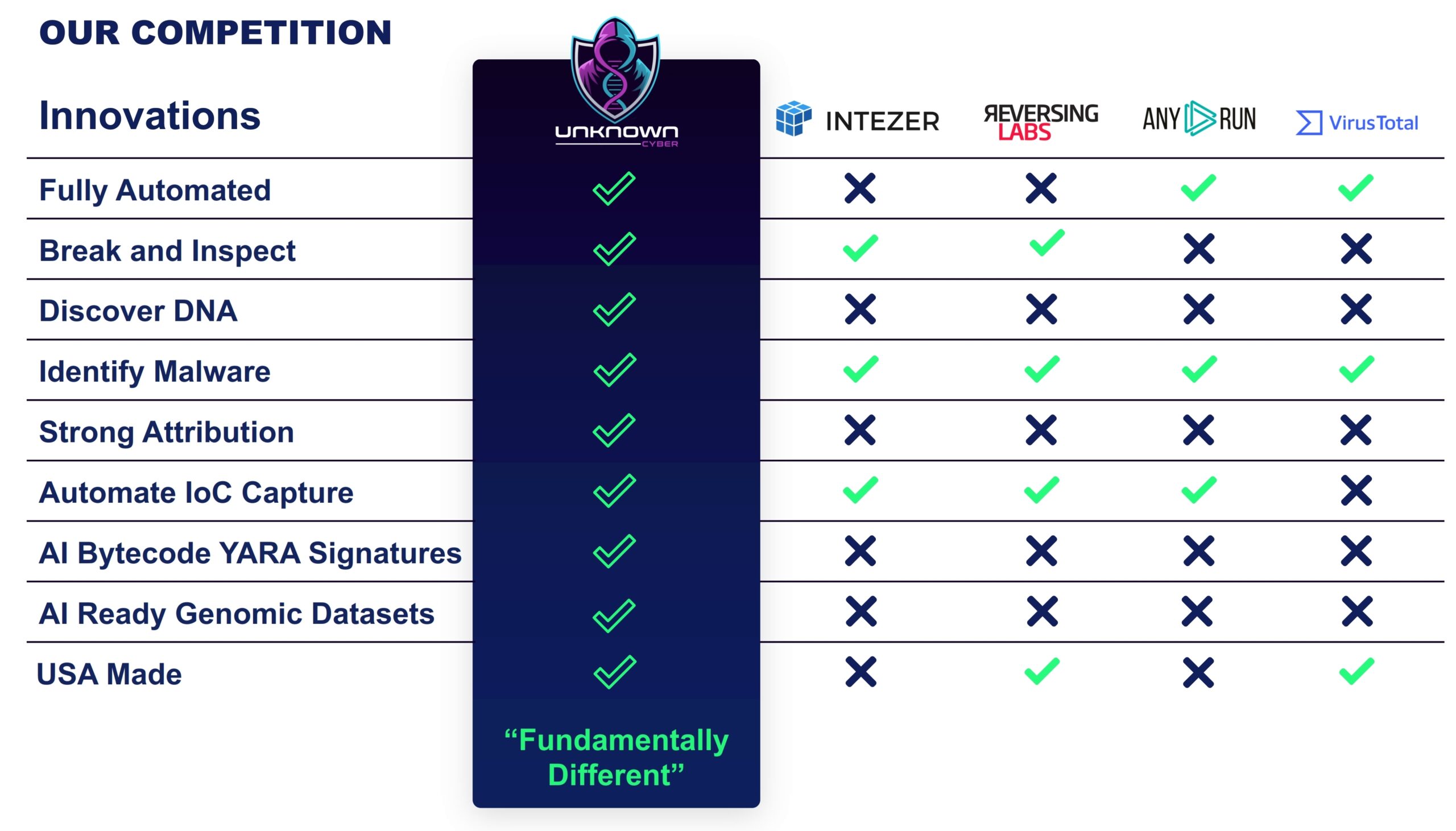
UnknownCyber Arsenal
UnknownCyber combined four powerful disciplines into one unified platform:
- An interactive sandbox (JUCY) with evasive malware detection
- Automated reverse engineering through bytecode genomic extraction
- Variant-level attribution across obfuscated and fileless threats
- Signature-quality YARA rule generation in seconds