ACCELERATE - DFIR
Unknown Cyber accelerates DFIR with genomic code comparison at the bytecode level, defeating obfuscation and detecting unknown variants for instant classification, precise attribution, and rapid response.
What do you get?

Genomic Analysis
Unknown Cyber Genomics detects, connects and attributes malware at the function level, uncovering unknown variants that evade AVs and sandboxes through advanced code comparison to create new threat intelligence faster with statistical classification that sees through obfuscation and can be used in evidence.

Genomic Sandbox
JUCY Sandbox integrates genomic analysis with traditional static and dynamic sandboxing techniques to rapidly deconstruct malware at the bytecode level, identifying evasion tactics and delivering threat intelligence exponentially faster than traditional reverse engineering.
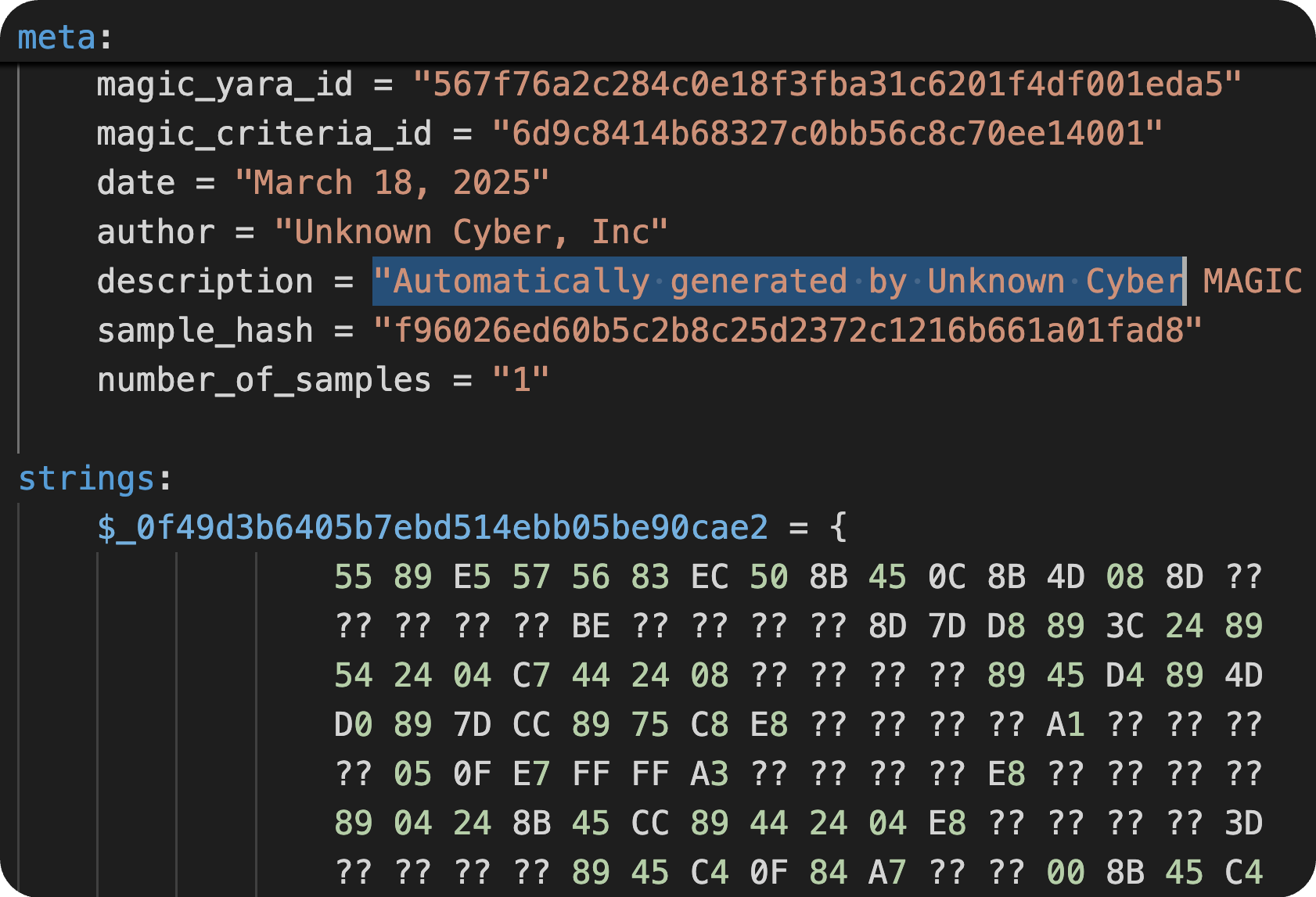
Automatic Bytecode YARA
Unknown Cyber's bytecode YARA rules are game-changing—they leverage advanced function-level genomic analysis to automatically generate the most accurate detection signatures, saving significant time. Unlike traditional string-based matching, they capture the true structural fingerprint of malware, exposing hidden variants and post-ransom payment plants, making them indispensable for modern threat detection.
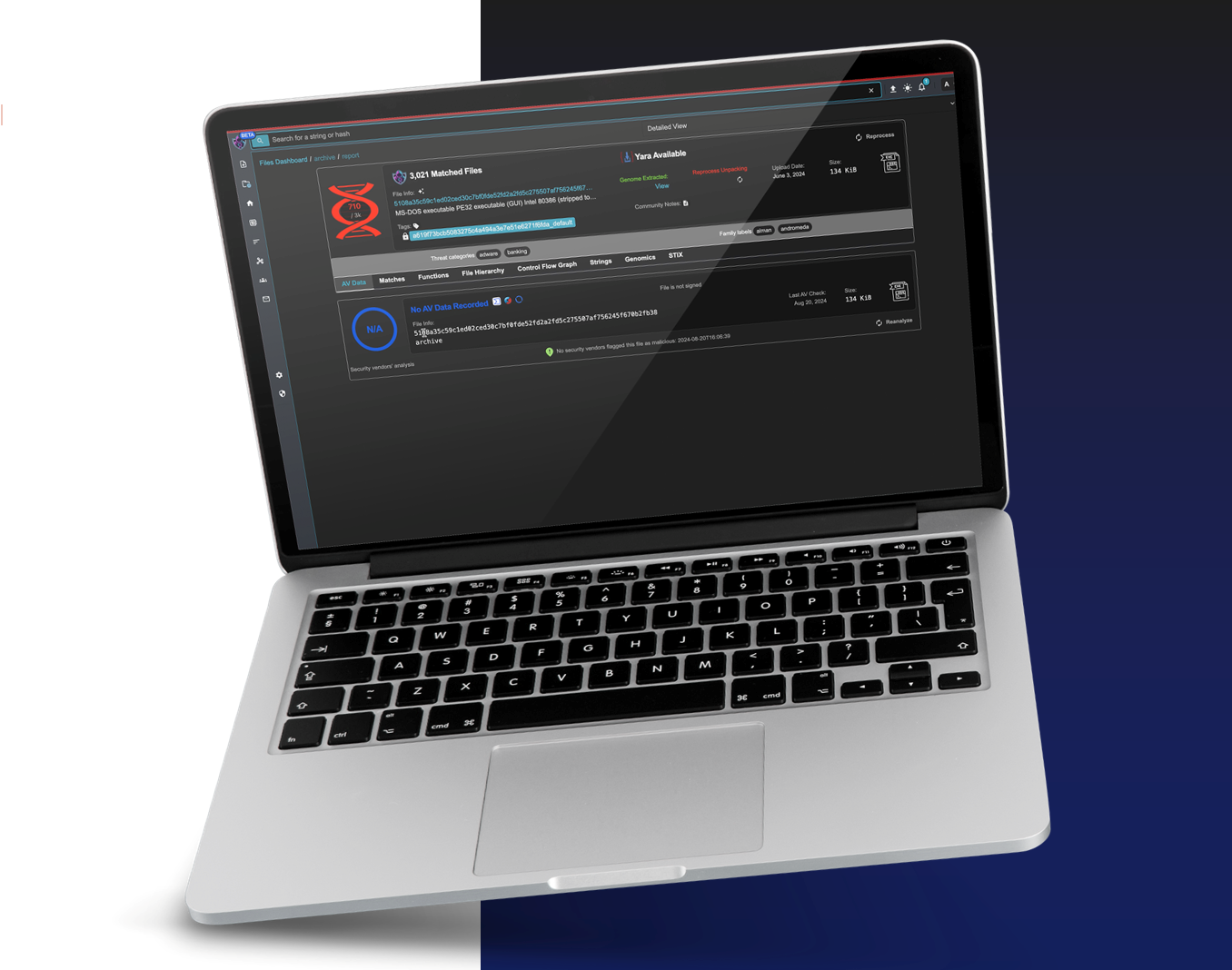
Portable Malware Lab
Enterprise users can bundle Unknown Cyber's Portable Malware Lab and genomic datasets to deliver rapid, on-site threat analysis. Its portability empowers incident response teams to identify never-before-seen malware, generate actionable signatures, detect emerging variants, and monitor for persistence—even in disconnected environments. Customers can also integrate their own datasets and notes from prior investigations to accelerate detection, as Unknown Cyber matches these references down to individual functions to confirm the presence of previously identified obfuscated code.
Bob Miller, COO Global Data Systems
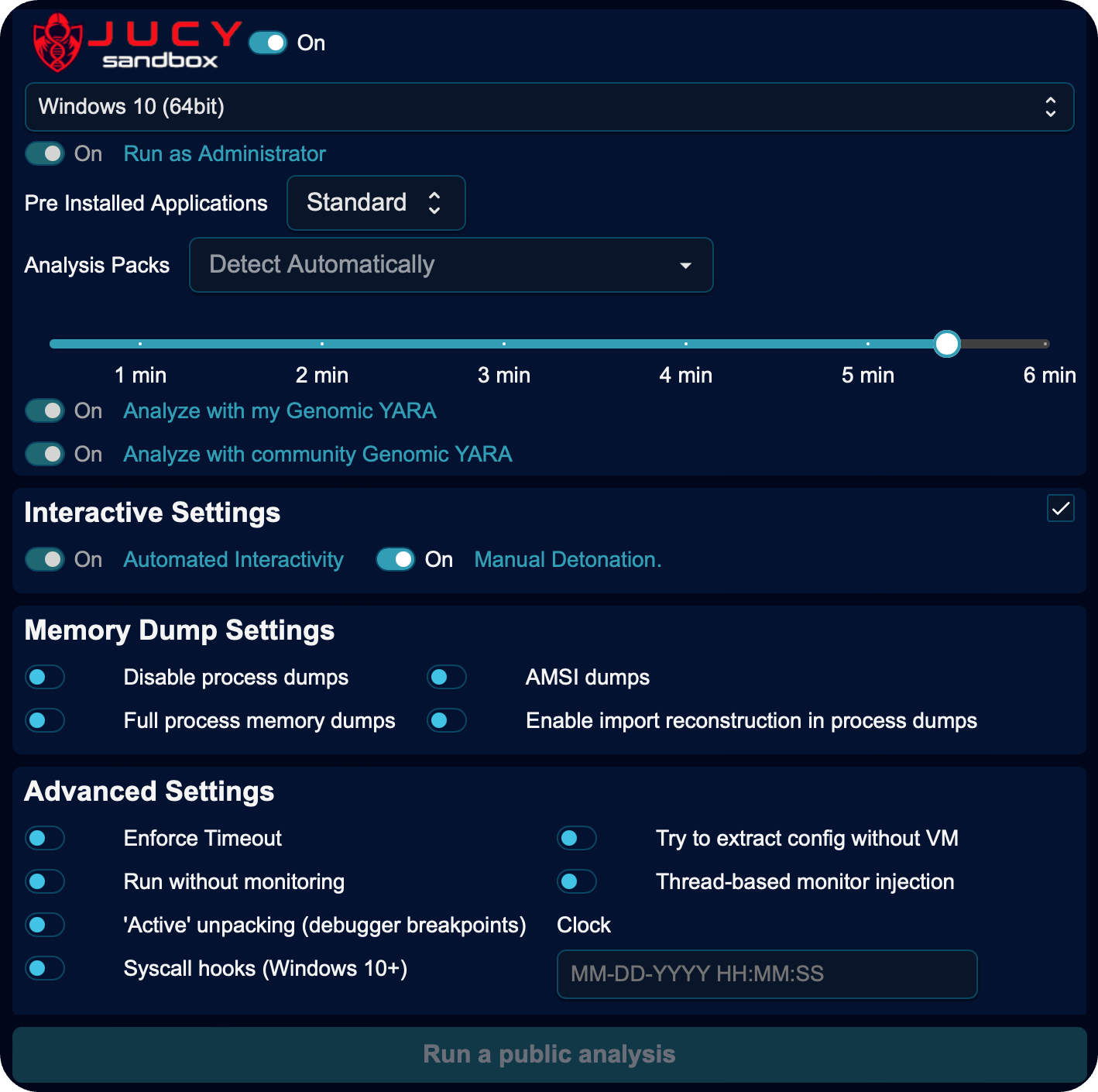
Fileless Malware Detection
JUCY Sandbox captures memory dumps during malware execution to automatically capture fileless malware and generate YARA rules that will detect variants of fileless malware operating solely in memory. These rules are archived with their corresponding attributed malware, creating a genomic library that offers threat detection capabilities not found in other sandboxes. When future unknown files are run through JUCY, their memory execution is inspected by these rules and, when triggered, the dropped files are automatically reuploaded to Unknown Cyber for comprehensive genomic analysis—performing deep function-level code comparisons with known attributed malware to detect fileless threats that evade other leading solutions.

Ask Bo!
Ask Bo is Unknown Cybers LLM interface engineered to interpret malware bytecode, delivering concise, human-readable explanations of code functionality. By focusing solely on the functional essence of the bytecode and filtering out irrelevant data, Ask Bo! overcomes common LLM challenges like token overload and excessive processing. This targeted approach streamlines reverse engineering, enabling cybersecurity teams to rapidly understand and respond to evolving threats.